Data Privacy and Protection in Telco 5G
Breaches Are The Rule, Not The Exception.
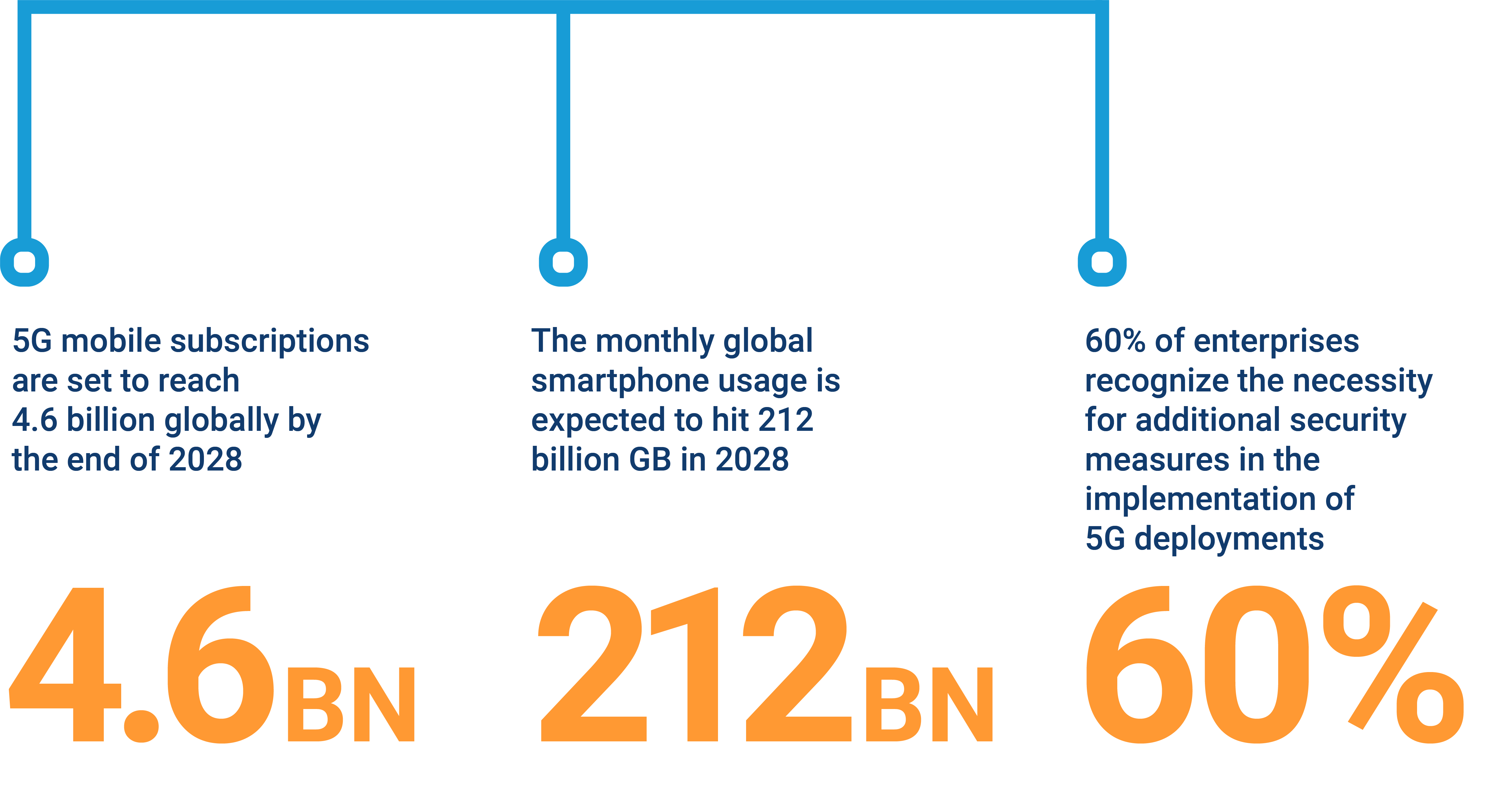
Telecommunication companies and businesses are shifting focus to the network edge and embracing cloud-native solutions amid 5G’s data transmission progress. Enhanced speed, minimal latency, and increased capacity promise transformative shifts, unlocking revenue through innovative models.
Data Confidentiality Remains the Primary Threat to Consumers and Enterprise Organizations.

Transitioning to NFV
In Network Functions Virtualization (NFV), functions are no longer on dedicated hardware but as Virtual Network Functions (VNFs) in shared virtualized environments, posing a risk of interference and malware cross-contamination, leading to data leakage.

5G MEC
For ultra-low latency in 5G applications, Multi-access Edge Computing (MEC) deploys applications at the network edge, posing challenges like reduced physical protection, local data storage, and secure encryption to meet latency demands.

Collaborative Resource Utilization
In IoT, edge-based data collection and analytics may lead to shared physical or virtualized infrastructure for telecom operators and enterprises. Precise isolation is crucial, demanding a clear separation of duties and finely managed perimeters to ensure security.
Zero-Touch Automation
Zero-touch automation in 5G, facilitated by cloud-native virtualization, enables rapid deployment but poses risks. It swiftly propagates both beneficial and harmful outcomes, challenging traditional data security assumptions, requiring enhanced measures in the 5G era.
